SiteAudit OnSite, Hosted, and Compact products support secure discovery and monitoring of devices using version 3 of the Simple Network Management Protocol, SNMPv3. This document describes how to configure SiteAudit discovery to find and monitor your SNMPv3 enabled devices.
By default, SiteAudit uses SNMPv1 since it is the most widely used protocol for communicating with networked devices. As organizations have become more security conscious, some have chosen to use a secure form of communication within their network. The device configuration for use of SNMPv3 is more complicated than that for SNMPv1. For example, to communicate using SNMPv1 one only need to configure the community string on the device, which is "public" by default. To configure a device to use SNMPv3 requires the device first be configured for HTTPS. Then one enables the desired authentication and privacy protocols, their passwords, a security name. The purpose of this document is to describe how to configure SiteAudit to communicate with devices that have already been properly configured for SNMPv3.
Process
for using SNMPv3 with SiteAudit
Once printers in the environment have been setup to use SNMPv3, SiteAudit discovery can be configured to find and monitor them. The following
overview describes how to use SNMPv3 in SiteAudit
- Enter SNMPv3 profile(s) in Discovery Configuration
- Configure the application settings to instruct SiteAudit to use SNMPv3
- Start the monitoring service
SNMPv3
Discovery Configuration
The image below
is of the SNMPv3 Configuration panel where users enter information used by SiteAudit to communicate securely with devices. The SNMPv3 properties can
be added, removed, or edited from this dialog. Use the up/down arrows on the
right to order the SNMPv3 profiles. The best practice
is to place the profile used most first in the list.
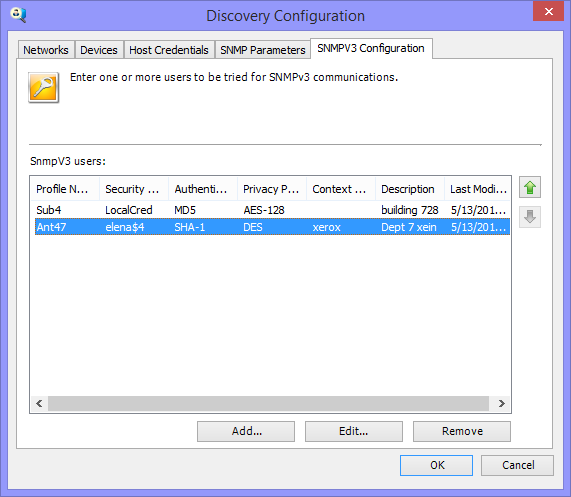
Ideally, all devices in an environment use the same SNMPv3 profile although it is perfectly fine to enter several SNMPv3 profiles. The best practice is to use as few profiles as possible, much like is suggested when entering community strings for SNMPv1.
Adding
a Profile for SNMPv3 Discovery
Clicking the Add
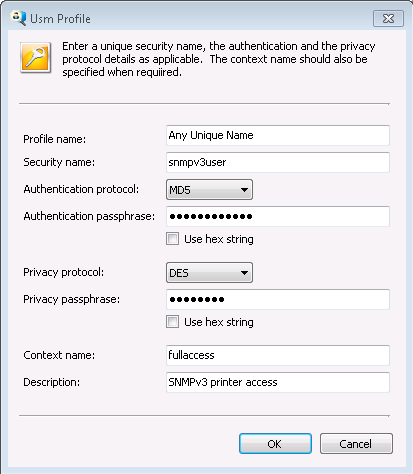
button in the SNMPv3 Discovery tab opens the Usm Profile dialog where a profile
can be created. A sample profile is shown below.
NOTE: For security purposes, SNMPv3 Profiles can
only be entered on the machine where the DCA monitoring service runs
USM
Profile
The user-based security model (USM) profile must
be specified for SiteAudit to discover and monitor SNMPv3 devices. A USM profile must be created for each unique SNMPv3
configuration in the environment. Ideally, all SNMPv3 devices communicate using the same profile. The following table defines the fields in the USM profile
|
Profile name
|
A unique name that describes the SNMPv3 configuration (mandatory) |
|
Security name
|
The USM security name configured on the device (mandatory)
|
|
Authentication Protocol
|
SiteAudit options include (none), MD5 and SHA-1, SHA-256, SHA-384 and SHA-512 authentication protocols
|
|
Authentication passphrase
|
A password is required when using authentication
|
|
Use hex string
|
The passphrase is constructed as a hex string
|
|
Privacy Protocol
|
SiteAudit options include (none), DES and AES128 privacy protocols. A privacy protocol can only
be used with authentication
|
|
Privacy Passphrase
|
A password is required when using privacy
|
|
Use hex string
|
the passphrase is constructed as a hex string
|
|
Context name
|
Allows one to limit access to portions of the MIB. Some devices have default context names such as jetdirect, xerox for some Hewlett-Packard and Xerox devices
*** SiteAudit requires access to the full MIB *** |
|
Description
|
User defined description for this profile
|
Valid
Configurations of Authentication & Privacy
There are three ways to configure SNMPv3
- No authentication and no privacy (noAuthNoPriv) - usually for monitoring
- Authentication and no privacy (authNoPriv) - usually for control
- Authentication and privacy (authPriv) - usually for downloading secrets
SNMP
Protocol Version Application Settings
By default,
SiteAudit is configured to communicate over SNMPv1. In order for SiteAudit to
perform discovery and monitoring of SNMPv3 devices, the SNMPVersion must be
changed in application settings. SiteAudit can
communicate using a single SNMP protocol or multiple protocols. When using
multiple protocols, each must be separated by a comma as shown in the example
below.
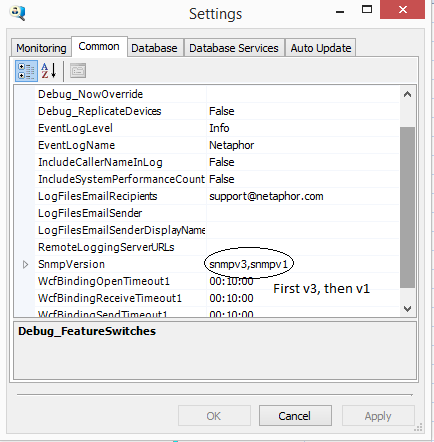
Sample
SnmpVersion Entries
The SnmpVersion application setting instructs SiteAudit to use a specific SNMP protocol. The table below shows each valid SnmpVersion option and describes its function.
|
snmpv1
|
Discovers and monitors SNMPv1 devices only
|
|
snmpv2c
|
Discovers and monitors SNMPv2C devices only
|
|
snmpv3
|
Discovers and monitors SNMPv3 devices only
|
|
snmpv3, snmpv1
|
Discovers devices that support SNMPv3 first and SNMPv1 next. SiteAudit first attempts to establish communication using SNMPv3. If the device is authenticated, then SiteAudit uses SNMPv3 communications. If the device does not support SNMPv3 or cannot be authenticated, SiteAudit will use SNMPv1 to communicate with the device. This type of discovery is used in an environment where devices may support both protocols or as a means of identifying SNMPv1 devices that should be configured for SNMPv3.
|
**Note that using
multiple protocols will slow the discovery progress as SiteAudit must test each
device to see if the first protocol specified is supported and if not, then
check the second protocol. This is done for each discovery profile.